Simple Rules to Protect Against Spoofed & windows.net Phishing Attacks
Recently I’ve seen an extended rise in usage of Microsoft Azure Blob Storage to host phishing websites targeting Office365 users. Websites hosted under Azure Blob Storage can be accessed using windows.net domains which will naturally add a convincing feature - valid Microsoft SSL certificate. This “feature” has high probability in masquerading the undergoing phishing attempt and allow attackers to successfully lure their victims into trusting the web page.
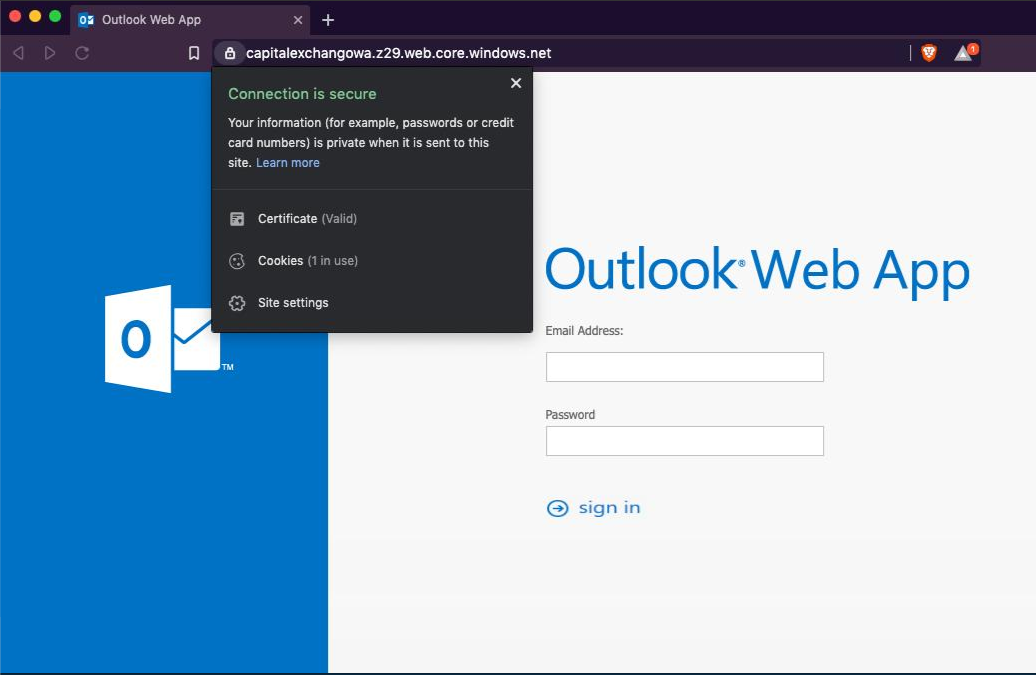
In addition, attackers tend to spoof the phishing email to look like it was originated from the user’s own email address.
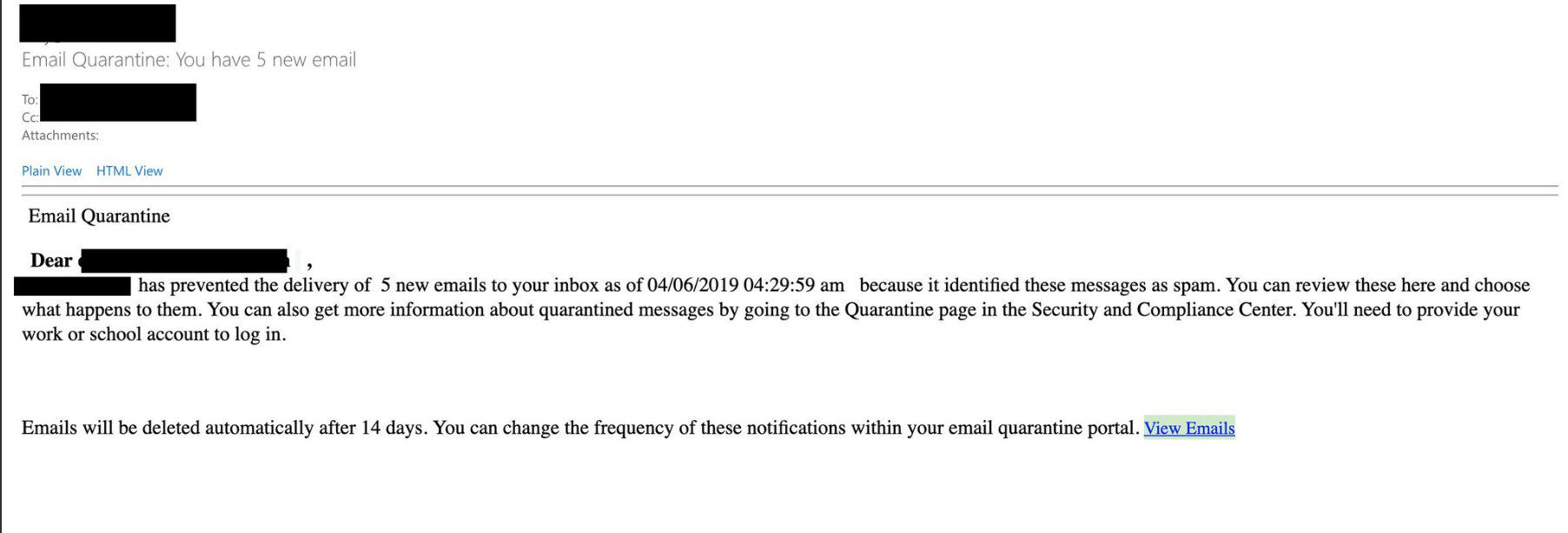
These tactics combined together have the potential of making this attack highly successful. Although this attack method is not new and has been previously reported, it seems like Microsoft is doing very little to prevent misuse of their services.
The thing that bothers me the most is that if you are using Microsoft Office365 premium security service “Office 365 ATP Safe Links” the Azure hosted phishing scams are marked as malicious.
Mitigation
In order to not rely on Microsoft in this case we can create two separated rules to block this kind of phishing attacks.
Creating Office365 Rules
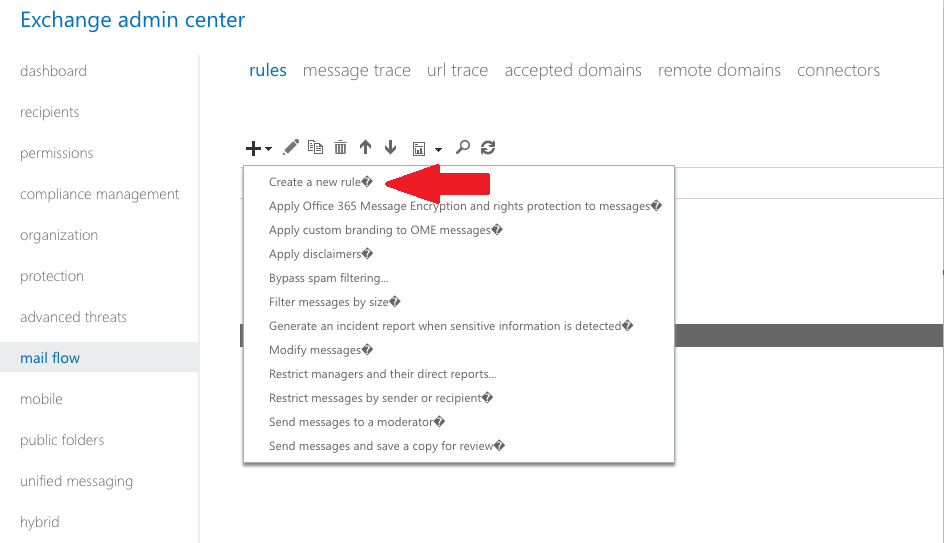
- Browse to Office365 Exchange Admin Center.
- Go to Mail Flow —> Rules then click on the ‘+’ sign and create a new rule.
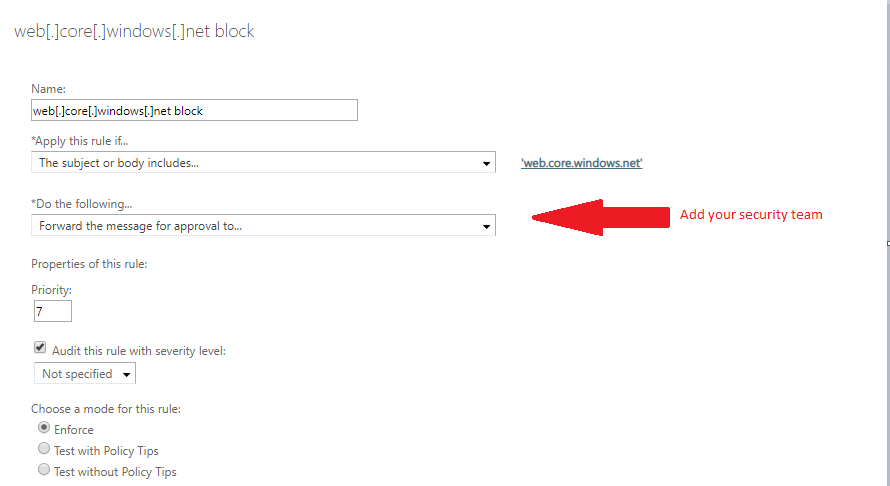
- At the New Rule section do as described in the image below:
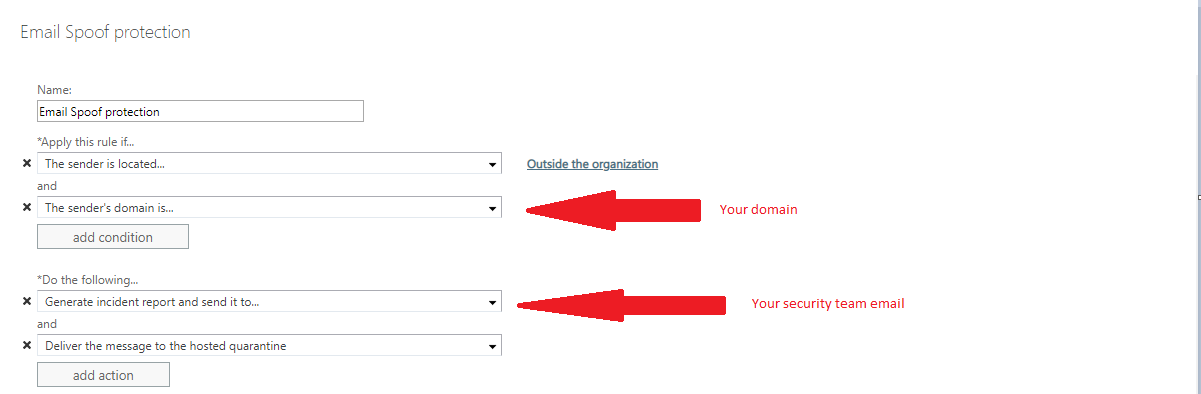
I recommend adding exceptions for automated email services such as build utils, marketing, etc.
Alerting users if email contains “windows.net” domain
- Repeat the previous steps to create a new rule
- At the new rule section do as described in the image below:
Blocking Spoofed Emails in Google Apps
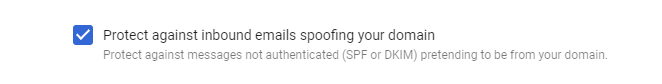
Although this article is more focused on Office365 users, I also recommend that Google Apps users do the same. Luckily, in Google Apps it’s much simpler than in Office365. Simply go to Gmail Safety Settings and enable the following rule:
These rules are not perfect but they can be helpful in protecting against this type of threat. I recommend inspecting how they might affect your organization before enabling them. In addition I would like to thank Sue & Corsin Camichel for their help in taking down some of these Azure Blobs.
References:
IOCs
hxxps://capitalexchangowa.z29[.]web[.]core[.]windows[.]net
hxxps://pitchbookoutlookowa[.]z29[.]web[.]core[.]windows[.]net
hxxps://office43l2v3rgq5y3xpy.z13[.]web[.]core[.]windows[.]net
hxxp://microsofpefzrydfaiv4tbz.z13[.]web[.]core[.]windows[.]net
hxxps://securitymailupdate.z15.web.core.windows.net
hxxps://fancy-prints[.]com/wp/ggfdd/index[.]php - post credential target
213.32.37.233 - fancy-prints[.]com resolve
hxxps://check[.]corequityholdings[.]com/validate[.]php
104.28.4.245 - check[.]corequityholdings[.]com resolve
https://pastebin.com/KUpiiKvR (slightly unobfuscated phishing source code)